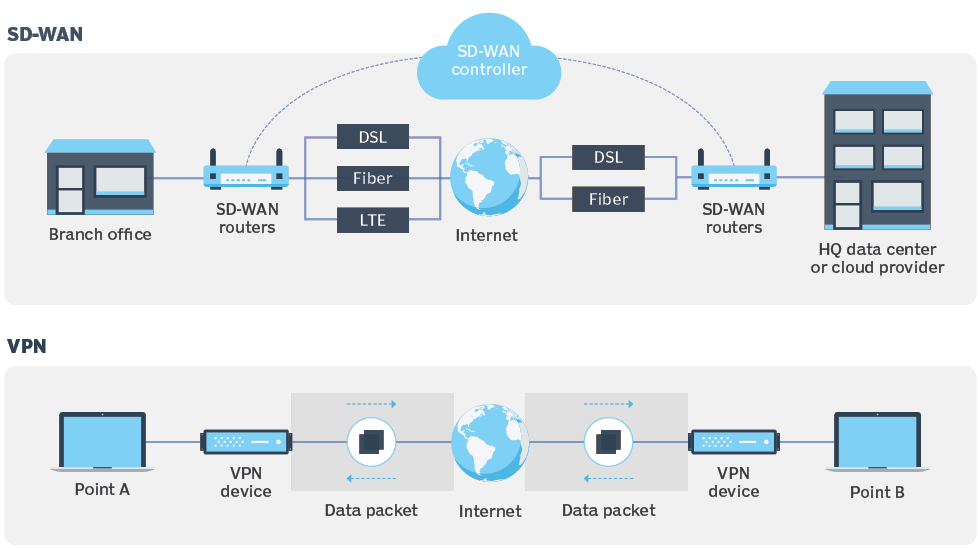
Connecting remote users into corporate IT resources has never been trivial. With
the shift to work from remote already well underway for many before 2020, the
global COVID-19 pandemic catalyzed the transition dramatically. The change
happened so fast, many organizations struggled to get their remote users
connected when working from