SD-WAN in a Work from Anywhere World
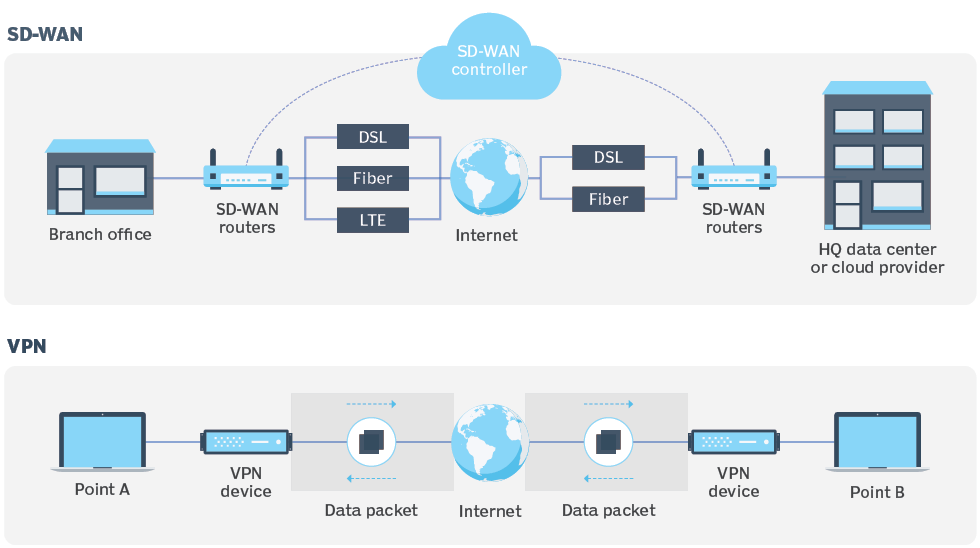
Connecting remote users into corporate IT resources has never been trivial. With the shift to work from remote already well underway for many before 2020, the global COVID-19 pandemic catalyzed the transition dramatically. The change happened so fast, many organizations struggled to get their remote users connected when working from home as it became a requirement. Remote access to an organization’s applications traditionally necessitates creation of a virtual private network (VPN) connection of some kind for these users to safely encrypt and secure access to sensitive data they need to do their jobs. We witnessed first hand our clients scaling this VPN demand up and having firewalls crashing from exceeding capacity, mad scrambles to upgrade licensing for more users, hastily getting software installed on laptops and needs to add cloud based VPN termination options to elastically expand capacity. It certainly was an eye opening experience for many that their infrastructure simply was not prepared to scale up quickly when they needed it most.
So how can we accommodate this sort of thing better in the future? With a bit of hindsight and introspection on what we just went through, are we as an industry thinking about remote connectivity in the correct way? Managing and securing remote connectivity for users can be achieved a number of ways, each of which having their own trade offs. There are some very progressive and forward looking models that are built with a “cloud first” mindset that do not require VPN connectivity. That said, I would say those are outliers in the corporate world today. Most organizations have a legacy application or other need to leverage a VPN for connectivity into their IT resources. Let’s explore a couple of methods of using VPNs for corporate connectivity and the compromises for each.
Endpoint Agent/Client Software
Many folks leverage an approach which involves a software client or agent running on the user device which will establish the VPN to “tunnel” a user’s traffic securely to and from the IT environment. Though very common and popular, is this the best way to connect users is a modern hybrid and multi-cloud environment?
The positive things about this approach:
- Most organizations have a firewall and the functionality to connect users via VPN is often already baked in.
- No additional hardware is required outside of the firewall and the endpoint itself.
- Sometimes VPN software agents inspect traffic before it enters the tunnel so it can be inspected before sent into the corporate network. This puts the security perimeter very close to the user.
- This is a well understood and a very common deployment scenario.
- User identity, and therefore access policy, is known and can be managed by nature of the user logging into the machine the agent is hosted on.
The negative things about this approach:
- Certain devices can’t run endpoint software (iOS, Android, unsupported and older operating systems, etc) so using phones, tablets and older computers may not be an option.
- Agents are putting the burden of inspecting, securing and reporting network & application usage on the user device which may consume compute resources taking away from the user experience.
- Managing permissions and controls on the user device can be difficult and time consuming.
- Hybrid, multi-cloud and SaaS network connectivity needs become complex to manage and secure.
- Additional licensing costs may be required to add users.
- Lack of network visibility without additional tools on the device.
So we get VPN connectivity included with components we may already have, but there are some reasons why it is not a one-size-fits all model. Let’s contrast it with an alternate approach.
SD-WAN Network Appliance
Another approach for remote users to access IT resources is leveraging an actual network appliance to terminate the WAN connectivity and then connect the user device via Ethernet or Wifi. Many platforms have SD-WAN capabilities today, not to mention some security features baked in so let’s assume we are working with these modern edge appliance features for the sake of our argument.
The positive things about this approach:
- Offload the tunneling, security, monitoring and visibility into a dedicated network appliance
- As long as a user device can get connectivity to Wifi or Ethernet, they can use it. This includes mobile and older devices.
- Many platforms can leverage authentication, authorization and traffic accounting to authenticate users and restrict them to appropriate resources.
- 4G/5G/Starlink connection resilience can be provided on demand, seamless and invisible to user. For businesses that require no downtime, this is crucial.
- Can perform enhancements like forward error correction (FEC), packet duplication, packet buffering and steering to improve performance (even over single link).
- Dedicated packet capture and inspection capabilities and potential to host synthetic application performance measurement at the edge
- Network team has more overall visibility and control into exactly what is happening.
The negative things about this approach:
- Additional devices to install, manage and support
- Additional hardware costs
- Depending on the platform, additional licensing costs
- Without agent, cannot validate state of end user device before attempting to connect
- More planning and coordination with users to get network connected vs getting on Wifi/Ethernet and firing up a VPN client.
In conclusion, which is better?
So which is perferable? The age old “it depends” applies. In most cases, my design preference would be the SD-WAN network appliance. I may be biased as a network practitioner, but I predict we will find many moving to a network based approach for work from anywhere. As computing capabilities evolve and can be supported in smaller packages, remote users will have a little “puck” sized appliance that will give them access to network resources.
My key reasons for this are:
- Lack of requirements for a software agent allows for user device independence.
- No need to manage software on user machines i.e. no dealing with OS permissions issues, no keeping agent software up to date, no user performance impact from agent, etc.
- More network and application visibility/telemetry opportunities with network appliance that stream this info not to mention the ability to easily issue packet capture at the edge on network appliance.
- Though you will have some additional costs to install and manage the hardware, there are great options to automate and orchestrate this control, not to mention things like zero touch provisioning to stand them up. It can be argued deployment can happen more rapidly.
- In the future, the potential to install apps at the edge. Examples would be synthetic application monitoring and measurement platforms, application optimization, data synchronization, etc.
- WAN & application optimization tools to clean up performance are typically baked in to correct problems like packet loss, jitter and packet loss on the fly.
- Managing routing, access control, content filtering and other things that we typically depend on the network devices we use today are well known and easier to manage on network appliances.
What do you think? Which approach seems better to you for remote connectivity, agent software or SD-WAN? Please comment here or on social media with you thoughts. As always, thanks for reading and I certainly would appreciate any input you may have!

